AI-Powered Dark Web & Compliance Platform Built for MSP Revenue
Turn breach intelligence and compliance automation into higher MRR. Zero-PHI monitoring, automated SOC 2 / ISO / HIPAA reports, and multi-tenant visibility designed specifically for MSP operators.
Prefer text? Send SECURE to +1 (406) 382-9207.
Single pane of glass for dark web exposure, executive risk scoring, and compliance status across every client you manage.
Designed for multi-tenant MSP environments — not single-company toy scanners.
Built to Monetize Your Entire Client Roster
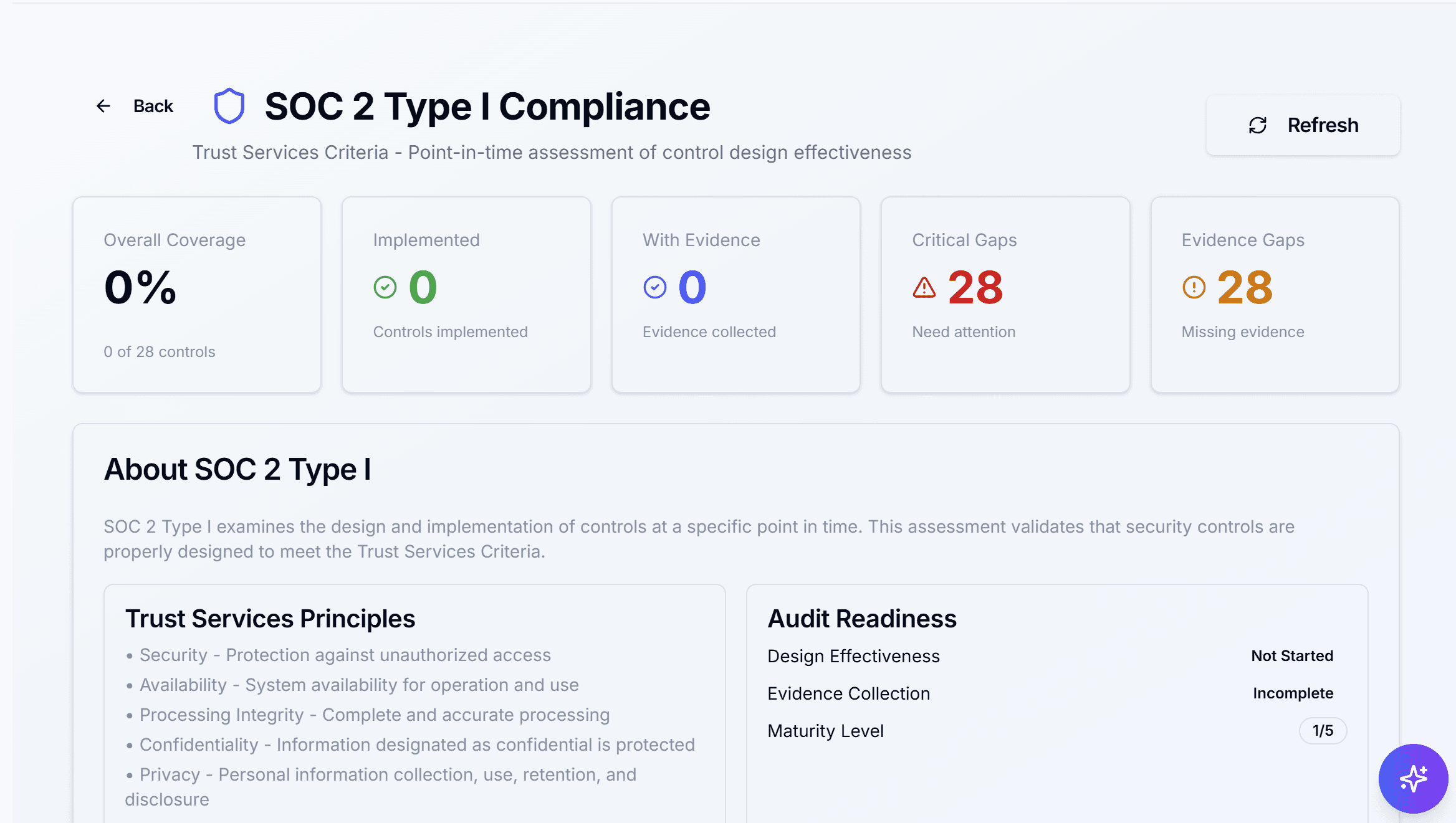
Product overview
A real MSP security platform: dark web monitoring, threat intel aggregation, automated compliance evidence, and actionable remediation — built to avoid invented data.
Dark Web Monitoring
Watch email domains, identities, and exposures — with evidence-backed results.
Threat Intelligence
Normalize incidents across sources and stream updates into a single feed.
Automated Compliance
Evidence collection + scoring for common frameworks (SOC2, ISO27001, HIPAA).
MSP-Ready Ops
Multi-tenant design, client isolation, and automation/worker-first workflows.